HARPP DDI™ (Deep DDoS Inspection) Technology
DDoS Mitigator’s DDI™ (Deep DDoS Inspection) Technology is designed to be your intelligent shield against DDoS attacks with Advanced Persistent Threat (APT) capabilities.
By its best of the breed anomaly engine with heuristic and non-heuristic algorithms supported by 34+ data sensors and innovative proportions feature based on historical data collections and timely averages, unpredictable DDoS traffics can be detected on real-time for cleaning.
| Real-time Inspection |
Real time traffic analysis
In time decision before DDOS
floods reaches to firewall |
| Data Sensors |
34+ data sensor groups under
4 categories
Advanced configuration
tool to make sensors fully controllable L7,
application level sensors |
| Static Thresholds |
By default generic static thresholds
experienced in different types
of networks, traffics and attacks |
| Dynamic Threshold Optimization |
Automatic optimization of sensor thresholds
based on
*threat level
*historical records archived on sensors |
| Proportions |
Network Memory
(Historical Data Collections)
Averages (annual, seasonal, monthly, daily,..) |
| Anomaly Engine |
Heuristic and non-heuristic algorithms
that use data sensor averages
Source determination of anomalous traffics |
| Geographical Traffic Classification |
Country based filtering
IP Block based filtering |
| IP Reputation |
IP itibar veritabanı sorgusu
5 seviyeli istisna listeleri (beyaz ve kara listeler) |
| DOS IPS |
DDOS pattern signatures for attacks
using application and system vulnerabilities |
| Deep Packet Inspection Firewall |
L7 Packet Inspection
Stateful Packet Inspection
Bandwidth Management
Ipv6 support |
Data Sensor Categories
During or after the cyber attack, DDoS Mitigator gives you the chance to deeply analyze the attack
using the deductive case evidences including attacker IPs, attacker country, attack type and duration.
On-the-fly Comparison of WAN/LAN Traffics
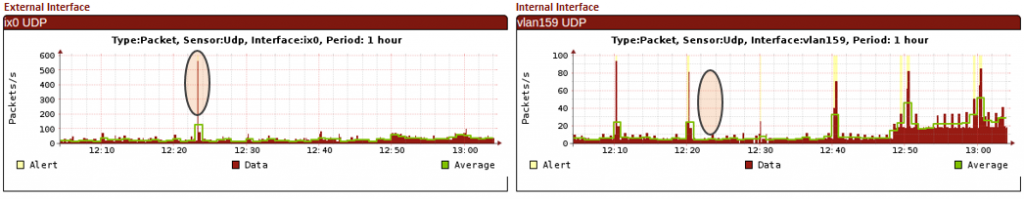
DDoS Mitigator is the first level of protection of your network against cyber attacks keeping you online and ensuring business continuity with minimal investment.
In addition to state-of-the-art defense functions providing high-level protection to your web and DNS infrastructure by its normalization, protection and protocol-specific security tools, preemptive defense functions are continually active day and night. The DDoS Mitigators all around the world create a wide security intelligence network you can access in real-time which is one of the key-differentiators.
Defense Functions
| Normalization |
IP Spoof scrubbing
Bogon IP scrubbing
Botnet zombie determination
TCP/IP protocol anomaly scrubbing
Packet defragmentation
DOS/DDOS packet generator tool blocking
Traditional DOS/DDOS tools blocking
(Teardrop, Land, smurf, fruggle, winnuke,
ping of death, oversized ICMP vb.)
URPF
Automatic aggressive session time-out |
| Mitigation/Prevention |
Time-out based on attack magnitude
Rate limiting
Packet dropping
IP/Network/Country blocking
Ability to give automatic access, only to
specific countries, white list, dynamicaly
produced frequent users, in case of
an emergency level exceeded
Challenge-Response Page |
| Protocol-Specific
Methods |
Robot detection and prevention methods
for TCP, UDP and DNS protocols |
Preemptive Defense Functions
| Coordinated
Mitigators |
Coordination of associated DDOS Mitigators
State, alarm, data, log sharing
Automatic ISP notification
IP reputation feedbacks
Setting Trap IP and port |
| Individual
Mitigators |
IP reputation feedbacks
Automatic ISP notification
Setting Trap IP and port |
Case Evidences & Forensic Analysis
| Attack Lists |
Chronologic attack list
Chronological subattack list
Attack filtering by
– interfaces
– attack type
– attack duration
– the beginning of the attack
– the end of the attack |
| Block IP Lists |
Searchable Blocked IP lists |
| Case Evidences |
Case evidence log file
Ability to work on evidence logs on
management screen
Ability to download evidence log file(pcap)
Attacker IP List |
| Filtering of block lists |
Filtering current blockages list by
– attacker IP
– attacker country
– attack type
– the beginning of blockage |
| Alarms |
E-mail/SMS notification
Attack report e-mail
Customizable alarms |
One of the key-advantages of DDoS Mitigator is its steerable and instantly tunable structure. During an intelligently-designed and complex DDoS attack, having a dynamic dashboard that visualizes the dynamic attacks is extremely important. DDoS Mitigator’s AVS™ (Attack Visualization System) provides multidimensional graphics where the deep attack characteristics can be fully monitored and analyzed to take the right steps in the possible shortest time.
Management and Reporting
| Installation |
Installation without changing the topology or
any other device configuration (no-change-deploy™)
‘Install-as-a-router’ Support
Interoperable with all standards-compatible network ‘
devices |
| User Interface |
Web based dynamic user interface for configuration
and monitoring
AVS™ (Attack Visualization System)
HTTPS/SSH Secure Management Support
Multilingual Management Interface
Operating system free management platform |
| Instant
Monitoring |
Dynamic dashboard with pre-configured graphs
(both for WAN and LAN interfaces)
Quick picture of the system
– Number of connections
– Number of states
– Number of unique IPs
– Packet per second value
– Bandwidth per second value
– System load |
| Reports |
Ready report templates
Reporting engine with parameters |
| Updates |
IP Reputation Database
DDoS Signature Database
DDI™ Engine
Advanced Firmware (Partially Upgradable)
No System Interruption for Firmware/Database Updates |
| Logging |
Internal Logging Area
Internal Evidence Collection Area
Trusted Time Stamp |
| Central
Management |
Remote Syslog Support
SNMP Support |
| Backup |
Automatic configuration backups
Restore the needed configuration easily |
One click away from deep
time-based analysis using
multidimensional graphics
(year/month/day/hour/min)

WAN & LAN
| Network Access |
TCP/IP (IPv4/IPv6)
Policy based routing
Link Aggregation (802.3ad)
Transparent Bridge Mode
VLANs (802.1Q) |
| WAN Interfaces |
Metro and Fiber WAN links termination on device |
| High Availability |
Flexible external / internal interface support
Clustering Support |


