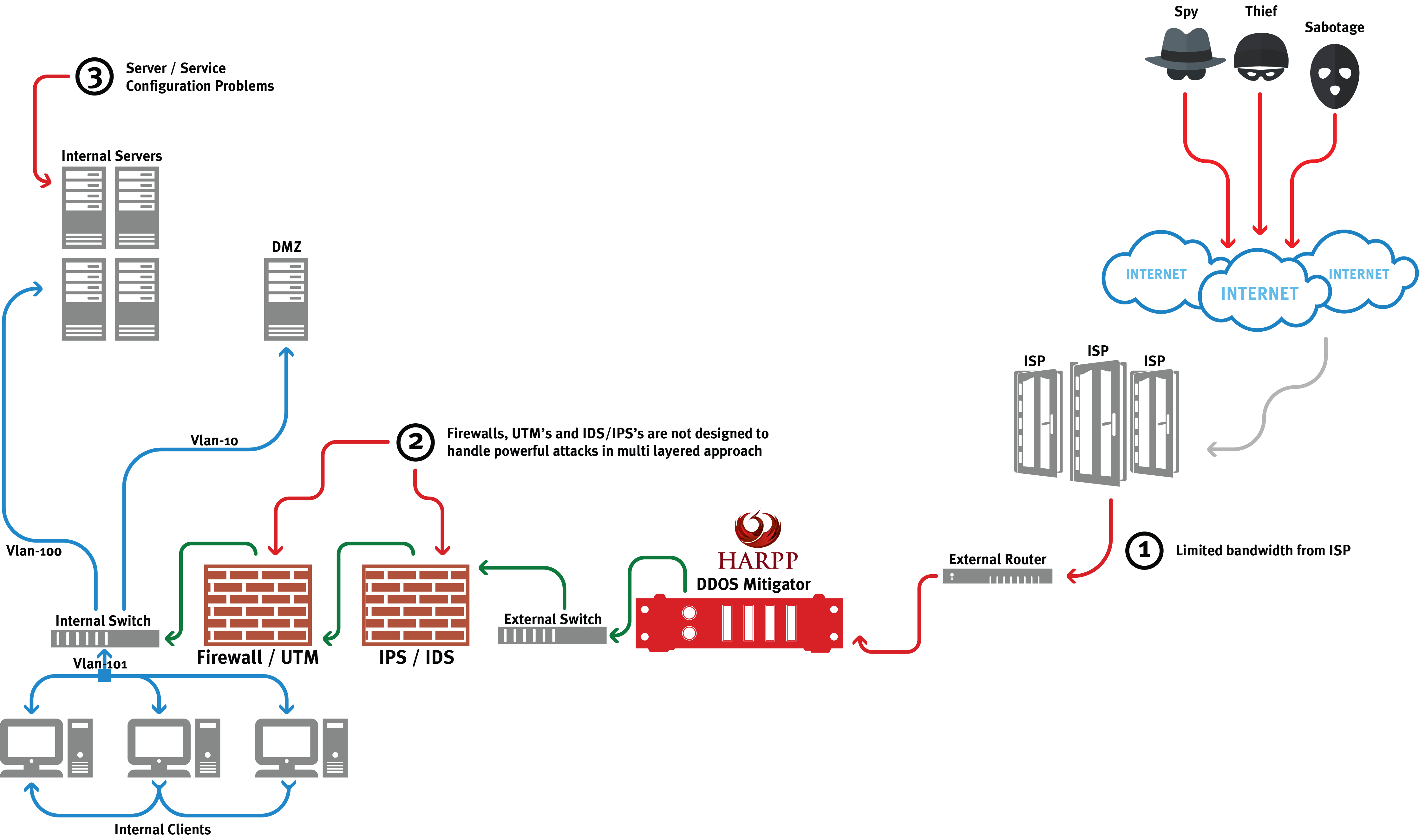
Inadequacies of DDoS service gotten from the service provider must be determined on the basis of attack levels and a dedicated product, capable to meet all attack levels, must be placed in the organization location.
DDoS attacks are carried out in the scope of all network layers. Against attacks, solutions which provide solution at all levels and capable to take attack decision by determining abnormal conditions using advanced algorithms rather than protection solutions depending on threshold values must be placed.
There’s almost nothing to do except ISP level in case internet bandwidth is smaller than incoming attack amount.
Attack content must be deepened for “high success” in DDoS attacks and a wide variety of attack prevention methods should be applied. 95% of DDoS attacks based on overloading today can be mitigated or completely blocked within the framework of this titles.
It is not possible to be completely protected against the attacks carried out in DoS and DDoS and continuously improved attack methods. The target is to minimize the effects at the attack time and take measures against the next similar attack beforehand.
In our DoS/DDOS appliance when taking attack decision, dynamic anomaly detection, threshold values and averages are taken into account. In only Fixed Threshold Value-based protection methods;
While network traffic coming above the Fixed Threshold Value (false-positive) can be prevented, attacks carried out by smart attackers, coming below the determined threshold (false-negative) cannot be prevented.
For this reason, Fixed Threshold Value-based protection methods are not adequate alone and adaptive threshold values protection is also enabled according to the network characteristics.
More than one parameters
- HTTP request / content-type distribution
HTTP challenge / response mechanism
- Setting and sending cookie according to structures like HTTP, HTML, JavaScript and Flash Player that should be in a real browser and redirect one of http message codes to client
- Blocking requests coming from only DDoS applications which do not have these structures